A Security Expert’s Take on the Trimble & FreightWaves Cybersecurity Report
Cybersecurity has become a growing concern for transportation companies as critical systems, devices and even vehicles become more complex and connected. In a recent collaboration between Trimble and FreightWaves, we surveyed transportation company leaders about the challenges, practices and trends they think are shaping the ever-evolving cybersecurity landscape in transportation, and released these results as our State of Cybersecurity White Paper. This is an essential resource for understanding transportation cybersecurity.
For deeper insight into the results of the survey and the white paper, we spoke with Conan Sandberg, Global Business Information Security Officer at Trimble. Below, he dives into the survey response statistics and offers his perspective on critical aspects of transportation cybersecurity, such as the adoption of cloud solutions, the impact of data breaches and much more.
Read the Trimble and FreightWaves State of Cybersecurity White Paper here.
Key cybersecurity challenges for carriers in the transportation industry
The white paper highlights several concerns for carriers when it comes to cybersecurity. What specific challenges do carriers face—especially small- to mid-sized carriers—when it comes to implementing and maintaining effective cybersecurity measures?
For larger carriers, they’re typically very aware of the transportation cybersecurity challenges that their operations present. But for small- to mid-sized operations, the risks are still very real and might go unnoticed until it’s too late. Regardless of an operation’s size, it’s critical they implement defense-in-depth strategies to cover user access points and IoT devices used, and invest in their cybersecurity program.
The volume of cyber attacks has only continued to increase over recent years, especially with the advent of AI, and the availability of digital systems to generate revenue is crucial to business operations. Investing in a cybersecurity strategy with business continuity needs to be a priority to be prepared, stay prepared and maintain system integrity to protect the users, customers and reputation of the organization. This is paramount for data security in the transportation sector.

Embracing cloud solutions for enhanced transportation cybersecurity
The report mentions that “the skepticism surrounding the security of cloud-based solutions that do remain are likely due to a combination of fear and misinformation.” How would you challenge this hesitation?
Cloud based solutions are significantly more scalable, cost effective, and allow for more streamlined disaster recovery/business continuity. Integration capability is critical for security tooling along with data feeds to cross connect products and services, which is a strong leading advantage with cloud-based environments, enhancing overall cybersecurity.
Now that over half of participating carriers have reported using cloud-based TMS, do you think this is a tipping point for the industry in terms of utilizing/prioritizing cloud-based solutions? For carriers that haven’t switched, how can utilizing a cloud-based TMS provide additional safety and data security?
Absolutely! For on-premise systems there are a few questions to ask: Do you have a geographically separated data center that is set up to cut over to in a short period of time? What would happen if your systems went offline today? I definitely think there is a tipping point for cloud based TMS solutions with the benefits it provides from scalability to flexibility with built in resiliency for the products. Using a cloud based TMS can provide additional safety with the ability to restore systems seamlessly to avoid down time in case of a cyber attack which can break SLAs invoking contract violations along with revenue loss.
The effectiveness of data security audits and modern cybersecurity measures
To your knowledge, how effective are recurring data security audits as part of a company’s overall cybersecurity strategy?
They can be very effective with ensuring validation of security controls in place while also providing guidance on gaps to cover. Audits are there to help ensure proper controls are in place to cover the various parts of technology confidentiality, integrity and availability.
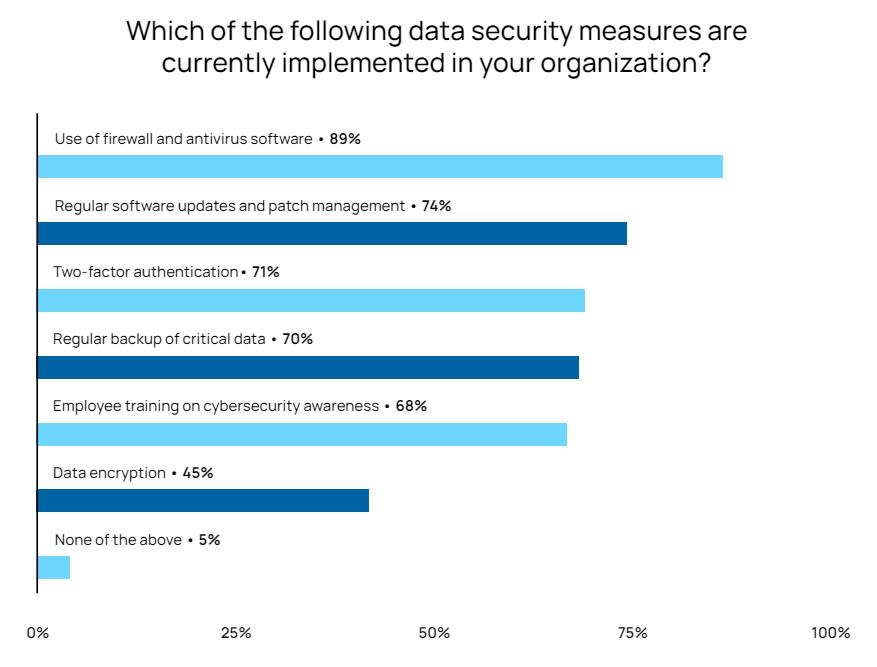
According to the report, the top data security measures used by companies are firewalls and antivirus software. Do you think this is the most effective approach for cybersecurity in transportation?
I think there are baseline security measures to have in place based on the risk appetite, Multi Factor Authentication, Endpoint detection and response and cyber security awareness training. These can enhance a cybersecurity program by enabling end users to be aware of cyber security best practices, respond to malicious activity with agents on workstations and prevent brute force password attacks.
Improving confidence and understanding cyberattack recovery time in transportation
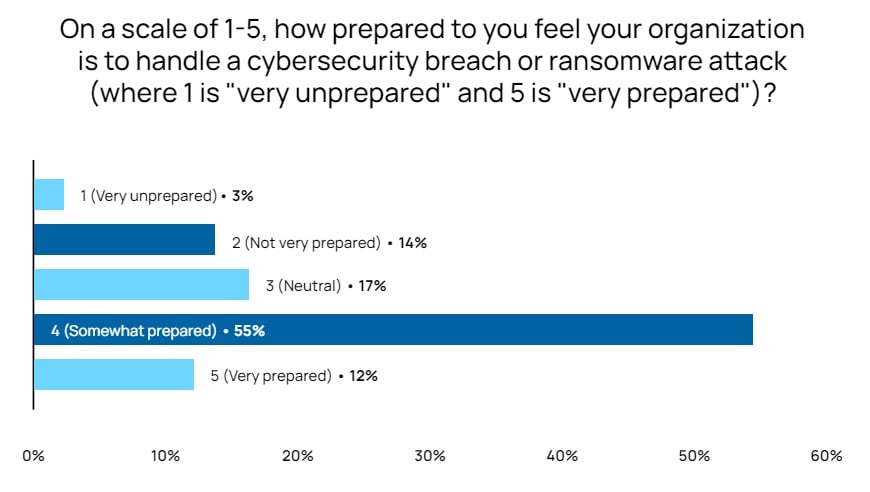
While the majority of carriers reported feeling “somewhat prepared” for a security breach, only 12% reported feeling confident or “very prepared.” What would be your number one recommendation for improving confidence in transportation cybersecurity?
A strong recommendation I would have is to outsource a Red Team agency or penetration testing company like White Oak Security, NetSPI or other external vendors who can simulate attacks and provide executive reporting which explicitly detail outlining areas of improvement. Table top exercises can also be effective and internally conducted to talk through a security breach to validate processes in place for response, remediation and recovery.
Finally, more than 60% of respondents thought a cyber attack on their business would be resolved in fewer than three days. Can you offer insight into the actual impact of a cyber attack and how long it takes companies to recover?
The time it takes a company to recover from a cyber attack can vary widely, depending on a number of factors, such as preparedness, cybersecurity policies, data backup systems and more. For instance, a well-prepared small company with policies that include regular audits, threat-sharing and a dedicated security officer could recover their business within days, while a large, less prepared company might be down for weeks or months.
On average, I think it will take longer to recover than the survey respondents expect. In my experience, with end-to-end discovery to containment to eradication and then recovery back to 100% operability, it takes several days or even months. According to a report from Statistia on the average number of days it takes a company to recover from a cyber attack, “it took the organizations 33 days on average to complete the forensic investigation of the attacks,” and I tend to agree with that report.
Nationwide reported two years ago that small- and medium-sized businesses are at the greatest risk of cyber attacks, as they don’t typically have the same protections as a large business. And in terms of cost, “cyber claims range between $15,000 to $25,000 in recovery costs, not to mention the length of time it could take to restore their brand’s reputation as they manage potential legal fallout during unassisted, lengthy restoration processes.”
That point about recovery time and injury to reputation is critical when it comes to the transportation industry. Every day a business is down, operations are impacted, trucks aren’t moving and revenue is lost.
Cloud solutions are the new frontier for cybersecurity in transportation
To learn more, read the complete Trimble and FreightWaves State of Cybersecurity White Paper.
Trimble is dedicated to our customers’ cybersecurity. To speak with us about how we can implement Cloud-based solutions that enhance your business’s cybersecurity posture, please contact our team.
Our focus on delivering reliable, scalable, and sustainable transportation technology solutions has made us a trusted partner for businesses seeking to achieve operational excellence and long-term success.
